Link Trace: A Comprehensive Guide
Link tracing, a crucial aspect of modern debugging and performance monitoring, allows you to trace the path of data or requests through a complex system. Whether you’re dealing with microcontrollers, web applications, or distributed systems, understanding how link tracing works can greatly enhance your troubleshooting and optimization efforts. Let’s delve into the intricacies of link tracing from multiple dimensions.
Understanding Link Tracing
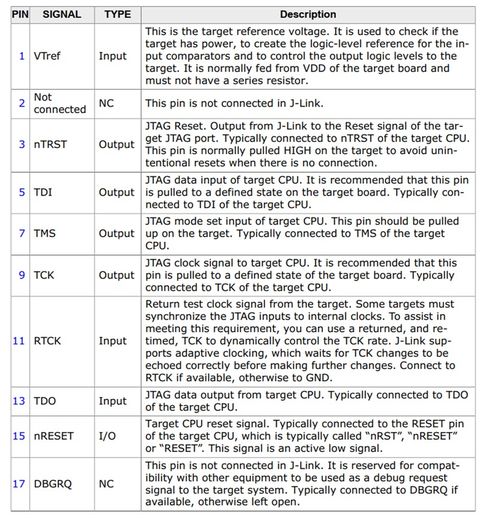
Link tracing, also known as trace debugging or tracing, is the process of tracking the flow of data or requests through a system. It’s a powerful tool for identifying bottlenecks, pinpointing errors, and optimizing performance. By following the path of data or requests, you can gain insights into how your system operates and identify areas for improvement.
Link Tracing in Microcontrollers
Microcontrollers, such as the STM32 series, often use debugging tools like J-Link to facilitate link tracing. J-Link is a versatile debugging probe that can connect to various microcontrollers, including STM32, and provide detailed information about their operation. Here’s a step-by-step guide to setting up link tracing with J-Link and STM32:
- Connect the J-Link debugger to the STM32 microcontroller using the appropriate cables.
- Open the J-Link software and select the “Target” tab.
- In the “Target” tab, choose the “Connect” option.
- Select the SWD or JTAG interface, depending on your setup.
- Select the correct chip model and debugger.
- Click the “Connect” button to establish a connection with the STM32 chip.
- In the “Target” tab, choose the “Unlock” option.
- Click the “Unlock” button to unlock the STM32 chip.
Unlocking the STM32 chip may result in data loss or damage, so it’s essential to back up all important data and proceed with caution.
Link Tracing in Web Applications

In web applications, link tracing is often used to monitor and optimize the performance of complex request paths. One popular approach is to use nginx as a reverse proxy and enable request tracing. Here’s how you can set up link tracing in nginx:
- Open the nginx configuration file (usually located at /etc/nginx/nginx.conf).
- Locate the “http” block and add the following configuration:
set requesttraceid httpxrequestid;set requesttraceseq httpxrequestreq;This configuration sets up a unique trace ID for each request, which can be used to track the request’s path through the system.
Link Tracing in Distributed Systems
In distributed systems, link tracing becomes even more critical, as requests often span multiple components and services. Distributed tracing tools, such as Jaeger or Zipkin, can help you track the flow of requests across different services and identify performance bottlenecks or errors. Here’s a brief overview of how distributed tracing works:
- When a request enters the distributed system, it’s assigned a unique trace ID.
- This trace ID is passed along with the request as it moves through different components and services.
- Each component or service records its operation and passes the trace ID to the next component or service.
- The entire request path is tracked and recorded, allowing you to identify performance bottlenecks or errors.
Link Tracing in Network Technologies
In network technologies, link tracing is used to analyze the path of data packets through a network. Tools like Traceroute can help you identify the route that data packets take from your device to a destination server. Here’s a brief overview of how Traceroute works:
- Traceroute sends a series of packets to the destination server with increasing TTL (time-to-live) values.
- Each packet is routed through a different router on the path to the destination server.
- When a packet reaches a router, the router discards the packet and sends an ICMP “time exceeded” message back to the source.
- The source receives these messages and uses them to determine the route that the packets took.
Conclusion
Link tracing is a powerful tool that can help you understand how data or requests flow through a system. By using link tracing, you can


















